Configuring LDAP Server Groups
The LDAP Server Groups table lets you configure up to
| ■ | Control: To use an LDAP server for call routing, you need to configure the LDAP Server Group as a Control type, and then assign the LDAP Server Group to a Routing Policy. The Routing Policy in turn needs to be assigned to the relevant routing rule(s). You can assign a Routing Policy to only one LDAP Server Group. Therefore, for multi-tenant deployments where multiple Routing Policies are employed, each tenant can be assigned a specific LDAP Server Group through its unique Routing Policy. |
| ■ | Management: To use an LDAP server for management where it does user login authentication and user authorization, you need to configure the LDAP Server Group as a Management type. Additional LDAP-based management parameters need to be configured, as described in Enabling LDAP-based Web/CLI User Login Authentication and Authorization and Configuring LDAP Servers. |
| ■ | Management Service: To use two different LDAP server accounts for management where one LDAP account does user authentication and the other LDAP account does user authorization, you need to configure two LDAP Server Groups. Configure the LDAP Server Group for user authentication as a Management type and the LDAP Server Group for user authorization as a Management Service type. In this setup, configure all the user-authorization settings (i.e., Management LDAP Groups and LDAP Server Search Base DN) for the Management Service-type LDAP Server Group only, instead of for the Management-type LDAP Server Group. |
The following procedure describes how to configure an LDAP Server Group through the Web interface. You can also configure it through ini file [LDAPServerGroups] or CLI (configure system > ldap ldap-server-groups).
The device provides a preconfigured LDAP Server Group ("DefaultCTRLServersGroupin") in the LDAP Server Groups table, which can be modified or deleted.
| ➢ | To configure an LDAP Server Group: |
| 1. | Open the LDAP Server Groups table (Setup menu > IP Network tab > AAA Servers folder > LDAP Server Groups). |
| 2. | Click New; the following dialog box appears: |
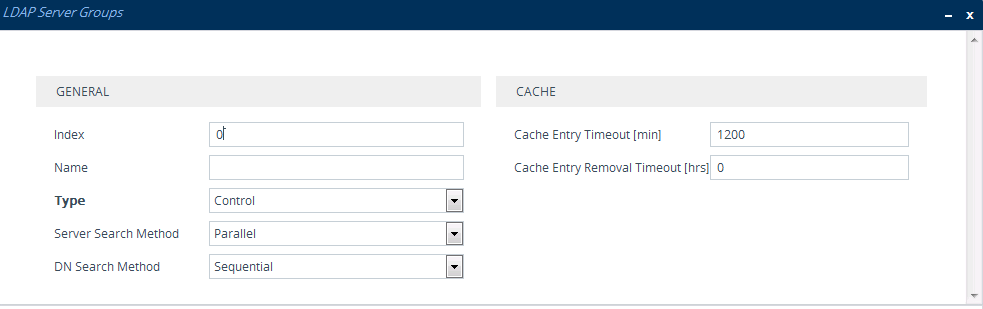
| 3. | Configure an LDAP Server Group according to the parameters described in the table below. |
| 4. | Click Apply. |
LDAP Server Groups Table Parameter Descriptions
|
Parameter |
Description |
|||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
General |
|
|||||||||||||||
|
'Index' |
Defines an index number for the new table row. Note: Each row must be configured with a unique index. |
|||||||||||||||
|
'Name' name [Name] |
Defines a descriptive name, which is used when associating the row in other tables. The valid value is a string of up to 20 characters. Note:
|
|||||||||||||||
|
'Type' server-type [ServerType] |
Defines whether the servers in the group are used for SIP-related LDAP queries (Control) or management login authentication-related LDAP queries (Management).
For more information on the different optional LDAP services, see LDAP-based Services. Note:
|
|||||||||||||||
|
'Server Search Method' server-search-method [SearchMethod] |
Defines the method for querying between the two LDAP servers in the group.
|
|||||||||||||||
|
'DN Search Method' search-dn-method [SearchDnsMethod] |
Defines the method for querying the Distinguished Name (DN) objects within each LDAP server.
|
|||||||||||||||
|
Cache |
|
|||||||||||||||
|
'Cache Entry Timeout' cache-entry-timeout [LdapServersGroups_CacheEntryTimeout] |
Defines the duration (in minutes) that an entry in the device's LDAP cache is valid. If the timeout expires, the cached entry is used only if there is no connectivity with the LDAP server. The valid range is 0 to 35791. The default is 1200. If 0, the LDAP entry is always valid. |
|||||||||||||||
|
'Cache Entry Removal Timeout' cache-entry-removal-timeout [CacheEntryRemovalTimeout] |
Defines the duration (in hours) after which the LDAP entry is deleted from the device's LDAP cache. The valid range is 0 to 596. The default is 0 (i.e., the entry is never deleted). |